What Are The Phases Of Threat Intelligence?
Here we are back again to the topic of security of data, networks and server. That is because the data security issues have increased to another extent and more companies and business are in search of safe and secure environment for their data as well as the provision of the alerts before the threats actually attack the system.
One of the latest ways to secure the system and data is Threat Intelligence. So what is it?

It is basically a refined form of information which is present in an organised and analysed way about all the present and future attacks which can threats the business to a greater extent.
Most of the organisations employ the threat intelligence for the reason that it gives an insight to the organisation about the external and internal risk or threat affecting the overall environment of the organisation. This intelligence will provide detailed information about threats which will assist the organisations to protect it from severe damages.
The intelligence has its own lifecycle which provides the raw information into something more insightful and detailed so that policymakers and issues handlers can deal with the potential concerns.
When it comes to intelligence concerning cybersecurity than the sources from which information is derived from two different categories technical and human sources.
Technical sources:
These are the sources which are based on the technology and the system such as servers, network traffic and files retrieved from the malware as well as private and public databases.
Human source:
As the name suggests, this category refers to any information which is related o human groups such as hackers, attackers or any other fraud groups. It can also be some social media groups, and information leakage when shared between two people or two industries.
Information from the technical sources is gathered in an efficient because of advancement in the technology, but when you have to look for the human source, then there is a need of human touch because technology cannot compete the mind of humans.
The threat intelligence lifecycle is similar to what has been employed for CIA intelligence lifecycle in general. The only difference is that this lifecycle will take into the security issues related to networks and servers.
The 5 Phases of Threat Intelligence:
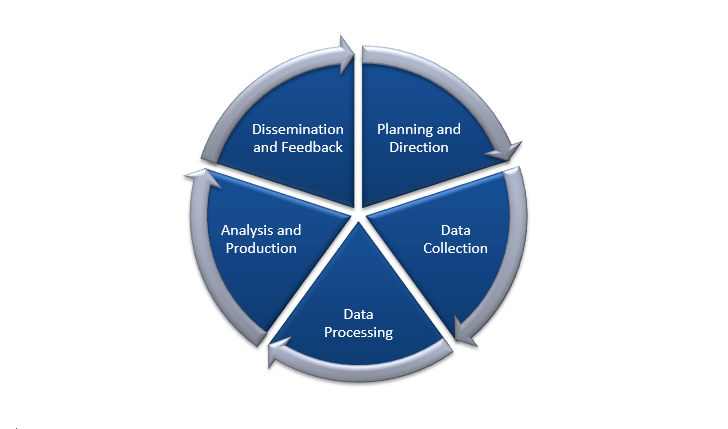
These phases are given below:
Planning and direction -
This phase is the provision of the information from a physical pace to a digital realm making it clear of what to do. When it comes to using this phase in the security check, then it will give proper information and direction to the threats which are related to networks.
Data collection -
Once the information is directed then the next opportunity is to gather data from both technical and human resources. In the manual process of data collection, there might be a million things to consider and data points to take into account. But with the help of threat intelligence and automation that comes along with it. Data from both public and private sources is collected because only public sources will not be able to provide the data in a full context therefore at times it is necessary to collect the private data of the company as well.
Processing -
Once the data is collected then the next step is processing the data. This phase also required automation for the processing purposes. The automation does wonders when it comes to detecting the threats, but the combinations of human and machines are going to bring even better results.
Analysis and production -
Just like security analytics, this techniques is also following the collection, processing and then analysis of the data. But in this step, the data should be organised and coherent. The threat intelligence is employed to understand the current behaviour and threats as well as look out for future prediction and warnings which can put the business or the whole network at risk.
Dissemination and feedback -
Once the data are processed and analysed for future predictions then now it is time to disseminate the information gained. The cyclic process will start again which means that based on the first cycle the new cycle will be modified and will provide insight on what was lacking in the previous cycle and how you can repair it.