Effective Tips To Find Security Consulting Companies
Have you ever heard about security consulting? Do you want to know why it is essential to get such services? Well, the purpose of writing this piece of information is to let you know some important facts regarding it.
Furthermore, this article provides tips that will be helpful for you in finding a good security consulting firm.
What Is Security Consulting?
First of all, you need to know the reality of security consulting. The term refers to the services that you get from a specific company to keep your information safe. This business is unique that is different from some regular companies that are providing IT consultation services.

IT services include only one specific area, on the other hand, consultancy covers security of the organisation and its prospective customers. The company reviews your assets and services, assess them, and then suggest some preventive measures.
Furthermore, the adaptation of these services allows you to monitor your security measures and protect your company from any kind of risk and threat.
Why Is It Important?
Why getting security consultancy is essential? This question may arise in your mind; however, the answer is quite simple. It is necessary for a company to secure their business related information as well as they need to secure the database of their consumer. No one has a desire to work with a company that cannot keep the confidentiality. In fact, it is the core of a company. Also, the loss of information may cause unbearable loss of identity and money.
Effective Tips for Security Consultancy
Sometimes companies cannot secure their information, and they require the help of an outside resource to meet the challenges related to information security. This is the place where the need for security consultants reconsidered.
Following are some of the useful tips that will be helpful for you in selecting proper security assistance. In this way, you will be able to work efficiently with the security consulting KSA firm to secure your company and bring essential benefits to rationalise the expenditure.
- The first and foremost tip is the understanding of your requirements. Just like self-awareness, it is important to aware of the services that you need. You need to adhere to the demand for which you need consultancy. For example, some of the companies do not know the type of evaluation that they require. However, reputable consultants assist them in figuring out the main problem. But it is essential for them to be prepared for.
- Another tip that you should follow while getting security consultancy is to gain access to different companies that are providing related services. In this way, you will gain access to multiple perspectives on the approaches that can be used to solve the problem. In addition to it, you will get an idea about price estimates.
- Build rapport with employees, who are working on your project. It will help to achieve better and desired results.
- Confirm if the expertise of the team members matches your requirements. You may get a clear idea through their past projects and certifications. There is the possibility that the hired company is itself a brand, but still, it is your responsibility to ensure that the consultants will be supportive of you in accomplishing your goals.
- Don’t just focus on the hourly rates for the project of security consultancy, emphasis on the overall cost of the project. The fixed price will be helpful for you in achieving unexpected results. Furthermore, you should do pricing on time if you want to be more explicit in your success. In addition to it, never forget to consider travel expenses.
- In addition to it, you should request an advanced project plan which includes milestones for the expected deliverables. It is noticed that some companies just focus on the initiating date of the project and they forget to plan an ending date and other checkpoints in the timeline of the project.
- Last but not the least; keep an eye on all critical aspects of the project. No doubt, the services of security consulting firm provide such oversight, but you also need to keep an eye on the plan to ensure its progress. It will be helpful in making corrections if any error exists.
Conclusively, companies should get the services of security consulting firms to secure their information and business. It will be helpful to boost their productivity and overall business with better customer services.
Get The Edge in Securing Business Information
What would be construed as the best practice in managing information security? The governance at every level of management must be strictly outlined keeping in view an established protocol need to be enacted that can ascertain the strength and weaknesses of the system. The decisions related to managing the security of information are strategic in nature. The ‘ifs’ and ‘buts’ that cross your mind must be adequately answered since the stakes are significantly high.
ISO 27001 Qatar is a dedicated and established protocol that checks the health of the information by outlining different threats and mitigating it. The advantage of having a certified protocol will develop a robust response mechanism. The various challenges related to the security of the information will be dealt with effectively.

The level of knowledge sharing is increasing substantially. Therefore, the connectivity is also amplifying on the network. The security of information is a significant concern for organisations. Data is regularly shared; you need to build parameters that can assess the impact of data sharing on the network. The value of information is different in diverse business contexts.
This requisite designing procedure for resource allocation that can fulfil the business objective have you taken appropriate measures to protect information? The environment is the platform that determines the design procedure of information sharing. The variable intrinsic value of the accumulated data is the part of the total intellectual capital generated. The application of devising qualitative procedures is significant as the demand for data protection has increased multiple folds.
Risks are numerous; the need to avert the dangers is intense. What can be done about this? IS0 27001 Qatar builds an accountability procedure that corresponds with the scope of the business and provides transparency in outlining and reducing different types of threats.
See Also:
What Are The Phases Of Threat Intelligence?
Here we are back again to the topic of security of data, networks and server. That is because the data security issues have increased to another extent and more companies and business are in search of safe and secure environment for their data as well as the provision of the alerts before the threats actually attack the system.
One of the latest ways to secure the system and data is Threat Intelligence. So what is it?

It is basically a refined form of information which is present in an organised and analysed way about all the present and future attacks which can threats the business to a greater extent.
Most of the organisations employ the threat intelligence for the reason that it gives an insight to the organisation about the external and internal risk or threat affecting the overall environment of the organisation. This intelligence will provide detailed information about threats which will assist the organisations to protect it from severe damages.
The intelligence has its own lifecycle which provides the raw information into something more insightful and detailed so that policymakers and issues handlers can deal with the potential concerns.
When it comes to intelligence concerning cybersecurity than the sources from which information is derived from two different categories technical and human sources.
Technical sources:
These are the sources which are based on the technology and the system such as servers, network traffic and files retrieved from the malware as well as private and public databases.
Human source:
As the name suggests, this category refers to any information which is related o human groups such as hackers, attackers or any other fraud groups. It can also be some social media groups, and information leakage when shared between two people or two industries.
Information from the technical sources is gathered in an efficient because of advancement in the technology, but when you have to look for the human source, then there is a need of human touch because technology cannot compete the mind of humans.
The threat intelligence lifecycle is similar to what has been employed for CIA intelligence lifecycle in general. The only difference is that this lifecycle will take into the security issues related to networks and servers.
The 5 Phases of Threat Intelligence:
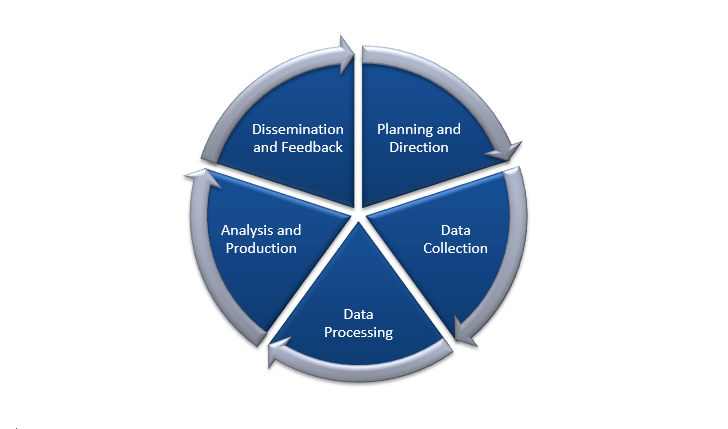
These phases are given below:
Planning and direction -
This phase is the provision of the information from a physical pace to a digital realm making it clear of what to do. When it comes to using this phase in the security check, then it will give proper information and direction to the threats which are related to networks.
Data collection -
Once the information is directed then the next opportunity is to gather data from both technical and human resources. In the manual process of data collection, there might be a million things to consider and data points to take into account. But with the help of threat intelligence and automation that comes along with it. Data from both public and private sources is collected because only public sources will not be able to provide the data in a full context therefore at times it is necessary to collect the private data of the company as well.
Processing -
Once the data is collected then the next step is processing the data. This phase also required automation for the processing purposes. The automation does wonders when it comes to detecting the threats, but the combinations of human and machines are going to bring even better results.
Analysis and production -
Just like security analytics, this techniques is also following the collection, processing and then analysis of the data. But in this step, the data should be organised and coherent. The threat intelligence is employed to understand the current behaviour and threats as well as look out for future prediction and warnings which can put the business or the whole network at risk.
Dissemination and feedback -
Once the data are processed and analysed for future predictions then now it is time to disseminate the information gained. The cyclic process will start again which means that based on the first cycle the new cycle will be modified and will provide insight on what was lacking in the previous cycle and how you can repair it.
Analysing EUBA as a Comprehensive Feature
The recent report of Mandiant [1], 2015 reveals that an average malware targeted compromise remained present for more than two hundred days before detection.
The longest period of a malware presence in the system is comprised of 2,982 days. Further, around 69% threats were detected by external security parties because internal departments of IT did not work properly.
It presents a dismal picture of security situations within organisations which has been accepted as a challenge to implement the sophisticated technology. So, the focus has been shifted significantly towards quick threat detectors to identify malicious users.
In response, user and entity behaviour analytics (UEBA) is emerged to mitigate threats by analysing malicious behaviours using Artificial Intelligence and Machine Learning.

The Situations where IT Security Professionals use UEBA
UEBA is considered a game-changer in the business industry owing to its rapid detection and stoppage of fraudulent attacks. It has become an integral part of retail stores and e-commerce.
It is owing to the reason that UEBA helps the organisations to identify and block hackers from signing in to major online sales and purchase web systems. However, it is very common to hack online shopping systems to steal credit cards and other credentials for vested interests.
For instance, a recent incident of hacking occurred at an air travel company where the intruders deteriorate the confidentiality using an affiliate network on Amazon Web Services.
As a result, the company had to experience more than 5,000 login attempts over the day through the stolen credentials. Thanks to UEBA, the malicious login attempts were blocked successfully.
So, the technology is amazing in thwarting fraudsters from getting access to retail systems and re-selling of stolen products.
It evident from the example of a popular gaming server, from where more than 2000 credit cards were stolen and around 500 users’ accounts were created new to use those credit cards. However, IT professionals used user identity technology to stop this massive fraud.
According to the latest report from Gartner [2], more than 60% of the overall organisations’ budget will be allocated to quick detections and threat response by the year 2020. It is the reasons that Endpoint detection and response or EDR is considered a hope for many business corporations.
Working Mechanism of UEBA
The idea is based on analysing profiling in order to detect an anomaly. It is done using machine learning technology and artificial intelligence.
So, the technology maps user activities in a legitimate process to look into suspected behaviours. In this way, threats are identified and stopped to make destruction in a system. The way how UEBA works is as given:
Data Analytics
It is the first component or step of the anomaly detection process. The system learns common behaviours and determines a baseline. Further, peer groups of profiles are built using simple flag anomalous patterns or behaviours. Data is analysed through a process of comparison.
Data Integration
Structured and un-structured information is categorized and assimilated in the form of data logs. Further, inspection of security information and configuration of network management is done using already established monitoring mechanisms.
Data Visualizations and Presentation
The technology manipulates powerful techniques and visual tools to detect recognized patterns of valid users and focus on infractions instead of wrong positives.
Benefits of Implementing UEBA
The technology has done more benefits in blocking insider attacks. It is the reason that Entity-Based Analytics tools are getting extreme popularity among private and public firms. The major role played by the techniques is as given below:
- Data is organized using identity association and patterns recognition
- Threats are detected using real-time analytics
- Artificial Intelligence and machine learning is used as the core technology which enables strict monitoring and malware hunting
- Effective integration of the technology with the underlying information platform
Concluding Remarks – Takes Away
To sum up, major security solutions are activity implementing UEBA to ensure effective data integrity. Gartner [3] predicts that approximately 80% endpoint protection platforms are expected to integrate forensics and AI monitoring by the end of 2018.
Taken together, EDR UK offers a wide range of security solutions to ensure adequate monitoring using UEBA to eliminate data threats.
Remember! Data breaches are becoming even more complicated as compared to the past. It is a dire need to understand hackers’ mind than their moves. So, intelligent means to ensure data security is a must for all and sundry.
Helpful Articles:
- 5 Most Common Network Security Threats
- Cyber Security: Facts And Trends
- Vital Steps In Cyber Security Analysis
References:
1.https://www.infosecurity-magazine.com/news/hackers-spend-over-200-days-inside/
2.https://www.gartner.com/newsroom/id/3638017
3.https://www.crowdstrike.com/blog/new-gartner-report-redefines-endpoint-protection-for-2018/
Why Is Security Consulting Important?
The world has never been more at risk of getting attacked than it is now. The security systems are getting smarter but so are the personals trying to break in. These attackers are sly enough to go undetected under an untrained eye, and have the credentials to attack multiple end points simultaneously.
What can be done to protect this? Get the most up-to-date security system and have professionals manage them. Some small scale businesses and individuals avoid getting security consultants involved thinking what is it that they can do and we can’t? Budgeting is another key reason as most security consulting service providers are quite expensive on the out-front.

But here we are listing all the reasons why you need security consultants:
Professionalism
In many firms and small scale businesses security is dealt with by personals, who hire outside help to install security systems like cameras, locks, alarm systems, etc. To a business mind, these steps might seem enough but under a threat of an attack, these would appear futile.
Management does not necessarily have an extensive knowledge of security systems and with the load of their other jobs; they hardly have the time to learn them.
What is the point of having a security system in place if it doesn’t work as effectively as you intended it to? This is where security consultants take the cake for their expertise is in the field. They can customize a whole security system depending upon your needs and requirements.
Prevention above Cure
Installing a new or updating an existing security system is often done in response to a specific security threat. Although dealing with existing issues is viable to a company’s safety, but reactionary security is not always as effective as preventative measures.
Exposed issues can easily be dealt with by forming a better security net, but a security consultant will be able to design a preventative plan that effectively fits a company’s security needs. An individualized and proactive preventative plan will intercept and react to a formerly unknown threat. Hence, averting the threat from even happening in the first place.
Risk Assessment
Most of the security threats are obscured by the onslaught of data received. The management often fails to notice such malwares and threats because of untrained eye. A security consultant, on the other hand, has been trained to do just that.
They will be able to analyze each data and identify and categorize threat and risks accordingly. This will help them mitigate a preventative or reactionary plan, determining the severity of the situation.
Constant Monitoring
Most professional security consulting service providers offer 24/7 video surveillance and access control systems. These scalable designs conform to local and international standards and can be integrated into existing security frameworks.
If the worst comes to action and your company comes under attack, they will be able to form a quick response team to help minimize the damage. The quicker the response time, the better your company will be able to recover and get back on its feet.
Evolving Needs
Security threats change with time and so does the systems installed to deal with them. Getting a security system, no matter how efficient, integrated into place is not a onetime solution.
As the growth in your business occurs, employees shift and rotate, and the landscape around your organization evolves, so would your security needs. No matter how good your current security system is, it will need up-gradation with time.
Acquiring the services of a good security consultant will ensure that you have a long term follow-up plan. They will do regular follow-up perimeter checks to ensure your security system is still up to the mark. This will help make certain that you are under no threat and your security needs are continuously being met.
Concluding Remarks
Your organizations’ security isn’t something that you should take lightly. Managing your perimeter control systems yourself may seem like an appealing idea for now but in the long run professional help is what you require.
Expert security consultants in KSA and UAE would not just have a more extensive and relevant knowledge of security systems available but they will also be able to monitor and analyze threats more viably.
They will be able to assess the risks you face in a more efficient way and ultimately help you prevent attacks from happening. Invest in a security consultancy now because your safety should always come first!
5 Most Common Network Security Threats
Organizations have fallen prey to network security threats and suffered unbearable losses because of their important data theft. There are many examples, technology giant Yahoo and sizeable financial institute Citi Bank being ripped off, losing a big part of their fortune, are amongst thousands of other security breach instances.
After a security breach at Yahoo in 2015, it was sold for only $4.8 billion, which was originally worth more than $100 billion before the security breach took place. We will not emphasize the importance of securing your data online; we will instead stress the importance of knowing these threats first. Data and information is the blood flow of every organization because it contains the personal information of your clients.

The professionals of cyber security UK or other European countries have equipped themselves with the latest security applications to address these threats effectively.
Virus
A virus is a notorious software that corrupts your hardware, data and other critical applications with a designed purpose. It can steal or erase your data, in some cases, it can even delete all the data from your hard disk.
It is a threat to your privacy because of its capacity of entering into your email and sending emails to your contact list on your behalf.
Rouge software
We often see a pop-up window that informs us about a new software update. It is designed professionally so that the users trust the credibility of this rogue software and click on the window. By clicking on the window, the software downloads on our system, and it starts corrupting our files. To address these security threats, managed security services UK are getting popular because they provide foolproof network security solutions.
Trojan horse
It is a malicious software that enters into your computer and starts controlling its operations. It is a powerful software that can even steal your password. It can take control of your webcam and start recording your movements.
Keylogger software
Cybercriminals develop this application to monitor the activities of their victims. Keylogger records every keystroke of the victim’s computer and sends all the information to the cybercriminals. However, this software is also available for parents and business owners to monitor the activities of their subjects.
Computer worm
It is a software that automatically copies itself from one computer to another. It replicates itself very fastly and creates countless worms. These worms take control of your email addresses and contact details and then send this infected worm to all the contacts.
As the contacts click on this email, their system gets infected. They have reportedly corrupted 8.9 million computers in just four days.
What Qualities Should Cyber Security Service Provider Possess?
Cyber security is really important for organizations in this era. They cann’t survive if they don’t have a proper security program that could help them remain safe from the modern day cyber-attacks. These attacks have been penalizing organizations from all around the world. That’s the reason every one of them needs to take care of the network security.
A proper network security system could secure them from the cyber-attacks. That will also keep their data and information completely safe from any kind of potential loss. Thus, they will keep functioning without any kind of interruptions. For such network and information security Dubai and the UAE based problems, we could find a lot of cyber security firms. Below are some of the qualities your cyber-security service providing firm should possess.

Clear Commitment Demonstration:
Most importantly, they should possess the qualities of that show thier sheer commitment towards their cyber security job. The accessibility and the confidentiality rules made by them should be strict, which could definitely restrict the employees from making any kind of bluffs.
Proper Risk Management:
Proper and necessary risk management is more than just an important quality. Without proper risk assessment and management, there is no benefit of a cyber-security firm. That is why, it is highly important for you to ensure that your firm possesses the quality of proper risk assessment and management as well.
Keeping the Confidential Information and Data Secure:
For the firms offering services to address cyber security UK -based and global issues, it is necessary to make proper arrangements so that all the confidential data and information could be kept safe from any kind of data breach.
Provides you Competitive Advantage:
Your firm must also possess some rare and additional feature which provides you a competitive edge over your rivals. That quality would actually make you stand out from the competitors, suggesting that you have a better information security plan as compared to the others.
Proper Security Structure Buildup:
A proper security buildup is very important to ensure remaining safe from every kind of cyber-attack. As cyber-crimes have diversified a lot and there are a lot of ways an organization could get affected by their attack, that is why a proper and an efficient security structure buildup is really necessary.
You Need Firewall Migration, No Need To Migrate Your Business
Introduction:
When things are not so secure just because one is more reliant on interconnected networks for business activities and is running the show online, negative factors like fear and de-motivation may take place.
These negative factors may push business owners in the hesitant zones, i.e. making it hard for them to make timely and stress free decisions that are fruitful in nature.
Easier said than done:
True, these tasks of moving on in an easy passion may not be as easy as they may sound. Therefore, one may look for robust IT security professionals who can provide one with managed security services and take care of complex tasks like firewall management, installing up to date security tools like anti-viruses, anti-malware and even running complex tests such as VAPT (vulnerability assessment and penetration testing).
Moving on without a backup:
Working on these domains without a robust backup may not help the cause and one may not find it easy. Gone are the days when limited and basic antivirus tools used to prove helpful in securing business’s online procedure to some extent.
Today the scenario has changed entirely; hackers and attackers are more focused on cyber world than ever before. They are keen to improve their skills and cope with the latest barriers, the idea of course is to breach the system and get hands on sensitive information of an organization and its clientele’s financial and personal data.
Awareness:
Most of the time, it is the lack of awareness from entrepreneurs while at times it is their intention to avoid such backups because they believe that things may prove costly. Which is not true to be honest, it is simply their lack of awareness, if one would consider the situation where one’s systems have been hacked and data has been compromised, one simply can imagine the uncontrollable loss that one may go through.
Firewall migration is another very complex task that may not be easy for one to execute in lone passion. Expert insights and backup may prove to be one’s best bet and things may only become easy, possible and dealt with in the right passion if such complex and highly sensitive tasks are outsourced to professional IT security agency that can rescue the situation for a business in the most reliable and affordable passion.
Conclusion:
To conquer the markets world over, you will need to operate with a free mind, if you believe you are not ready and are not fully backed with professional solution providers in the domain of IT security, you might as well hold your fire and hunt for the right backup before you pull the trigger.
Possible Challenges To Face When Setting Up A SOC
To keep up with cyber-security procedures is a threatening activity for organizations. Based on the nonstop innovations in cyber-attacks, implementing the required security plan are difficult. However, having a security operations centre is an ultimate solution to overcome the possibility of attacks on a network.
Security operations centres (SOCs) are the key requirements of the organizations that are operating confidential data of users. Such an optimal solution allows them to have a proper plan if a security incident happens. On the other hand, they also assist in incident identification regardless of the organization size and requirements.

Setting up a security operations centre is both a challenging and complicated task. No matter how much well-organized it is, a security operation centre such as UK SOC face certain types of challenges. Some of the major challenges they mainly face, include:
People:
Although finding out the best solution for improved protection is easy, however, employing the right people for proper execution is challenging. Even if you find the best experts with improved understanding of different elements in the same field, employing them will be expensive.
Security attacks are continuously happening with improved number these days. For protecting a given system, a security expert must have a clear understanding of the mutual connection between events. That’s how; it is difficult to find out experts having certain ideas of events at different levels.
Integration And Processes:
Integration with the rest of business operations is another challenge in setting up a security operations centre. They need to be technically integrated with other systems. A crucial feature of SOC is that it does not operate independently to react in an automated way against the recognized incidents.
Although certain service providers like security consulting KSA deliver optimal assistance regarding handling attacks on a well-defined order with the help of SOC. However, attacks and emergency management need a well-planned approach outside the technical integration of a security operation centre which is a bit challenging.
Technology:
All of the old-styled security information and event management tools are not sufficient to overcome the existing security needs. Although, they might match the rest of the solutions that are required for optimal protection, still they do not offer enough support on analytics and irregularity identification.
In this regard, real time security intelligence also known as RTSI is offering a collection of analytical abilities together with managed services. However, while looking for better protection, based on a higher demand of customers towards RSI, there is a noticeable limitation of their availability. It is a challenge as well, based on demand more than deliverable quantity.
London SOC For Secured Online Moves
Introduction:
Security has been a major concern for online business all over the world. Despite the fact that technological trends are roaring and highly dynamic because they are updating constantly, experts are still finding it hard to cap threats like hackers’ attacks and breaches for good.
Things are like this since beginning and it is believe that they will continue to be like this for ever because attackers are also keen to update their logics and moves accordingly with the growth of IT.

The right approach:
Dealing with such threats using free firewalls and antivirus without the professional assistance from an information security consultant is an idea dumped long ago by professional entrepreneurs.
Situation today:
It seems that entrepreneurs today have learned more about the seriousness and grave results that are usually associated with such mishaps. Awareness levels have improved greatly and they are more of the view to acquire professional services like managed SIEM, VAPT testing and security operation centres.
The idea sounds right because we are now in a world that is dominated by solutions that are offered to clients in real time. Prompt responses offered by robust backups that are provided by professional security consultants have changed the course of the game entirely.
Breaches are becoming difficult:
Hackers and attackers are finding it hard to breach the privacy and security of such organizations that are backed with elite solutions in the form of london SOC, managed security services and security services that are backed with artificial intelligence, virtual reality and real time solutions.
The cost:
There is this wrong perception that lives, i.e. opting for such security solutions may prove costly. Experts disagree with this simply because they compare the cost of these services with a situation where an organization may have not opted for such services and a breach takes place.
The company may have to go through grave situations and at times may even end up in paying fortunes just to compensate the loss incurred by its internal and external stakeholders. They therefore believe that paying a nominal fee just to stay away from such threats and unenthusiastic situation may help one as an entrepreneur in avoiding the aforementioned grave results.
Conclusion:
Security has been and will always be a major source of concern for business owners. Especially, those who rely heavily on their online presence that is depending on many interconnected networks. Obtaining help for reliable security consultants who can setup and monitor robust security operation centres for one’s business may be the right call at the right time.